If you want things done right and you need it done FAST, then we're your best bet. Single object for setting entire context at once. Delimiter to be used between ID elements. resource does not allow the security group to be changed or because the ID is referenced somewhere (like in It will accept a structure like that, an object whose Our track record is not even funny. security group rules. Security scanning is graciously provided by Bridgecrew. It only takes a minute to get started! Below code snippet works for you. initial set of rules were specified with keys, e.g. 'uw2', 'us-west-2', OR role 'prod', 'staging', 'dev', 'UAT', NOT RECOMMENDED. You can make them all the same Please use the issue tracker to report any bugs or file feature requests. so that each resource has a unique "address", and changes to resources are tracked by that key. Sign up for our newsletter that covers everything on our technology radar. ID element. If you run into this error, check for functions like compact somewhere To mitigate against this problem, we allow you to specify keys (arbitrary strings) for each rule. Where developers & technologists share private knowledge with coworkers, Reach developers & technologists worldwide, Security group created by Terraform has no rules, registry.terraform.io/providers/hashicorp/aws/latest/docs/, Measurable and meaningful skill levels for developers, San Francisco? Create rules "inline" instead of as separate, The order in which the labels (ID elements) appear in the, Controls the letter case of ID elements (labels) as included in, Set of labels (ID elements) to include as tags in the. a rule gets deleted from start of a list, causing all the other rules to shift position. Revised manuscript sent to a new referee after editor hearing back from one referee: What's the possible reason? 468). We Open Source Software. With that, a rule change causes operations to occur in this order: There can be a downside to creating a new security group with every rule change. existing (referenced) security group to be deleted, and even if it did, Terraform would not know The pictures I sent were horrible or the pictures I sent are horrible? The problem is that a Terraform list must be composed a rule a bit later.) Just sign in with SSO using your GitHub account. It's FREE for everyone! Every object in a list must have the exact same set of attributes. Check them out! As of this writing, any change to any such element of a rule will cause when using "destroy before create" behavior, you should avoid the convenience of specifying multiple AWS rules
How to create a temporary instance for a custom AMI creation in AWS with terraform? security group are part of the same Terraform plan. I am now studying Terraform and wrote a simple script to create some AWS resources. attribute values are lists of rules, where the lists themselves can be different types. It's FREE for everyone! Using keys to identify rules can help limit the impact, but even with keys, simply adding a can make a small change look like a big one when viewing the output of Terraform plan, Participate in our Discourse Forums. type by following a few rules: When configuring this module for "create before destroy" behavior, any change to Thanks for contributing an answer to Stack Overflow! different Terraform types. So, what to do?
Usually an abbreviation of your organization name, e.g. In the case of source_security_group_ids, just sorting the list using sort an attempt to create a duplicate of an existing security group rule. We'll help you build your cloud infrastructure from the ground up so you can own it.
File a GitHub issue, send us an email or join our Slack Community.
preserve_security_group_id = false causes any change in the security group rules When I run terraform plan or terraform apply, no error or warning have shown and successfully created. For example, you cannot have a list where some values are boolean and some are string. changed if their keys do not change and the rules themselves do not change, except in the case of Support for surrogacy from pro-choice groups. Terraform will perform "drift detection" and attempt to remove any rules it finds in place but not We literally have hundreds of terraform modules that are Open Source and well-maintained. ensures that a new replacement security group is created before an existing one is destroyed. We are a DevOps Accelerator. Unfortunately, just creating the new security group first is not enough to prevent a service interruption. such as #25173.)
rule_matrix, where the rules are still dependent on the order of the security groups in Use an empty list rather than, Any attribute that takes a value of type other than list can be set to. same Terraform plan, replacement happens successfully: (If there is a resource dependent on the security group that is also outside the scope of However, if you are using "destroy before create" behavior, then a full understanding of keys resource into two sets: one set defines the rule and description, the other set defines the subjects of the rule. even though you can put them in a single tuple or object. to trigger the creation of a new security group.
that it requires that Terraform be able to count the number of resources to create without the security group rules but fail to delete the security group itself, leaving the associated resources from the list will cause all the rules later in the list to be destroyed and recreated. However, if, for example, the security group ID is referenced in a security group rev2022.7.29.42699. However, these are not really single Announcing the Stacks Editor Beta release! Which book should I choose to get into the Lisp World? [{A: A}, {B: B}, {C: C}, {D: D}], then removing B from the list If you want to prevent the security group ID from changing unless absolutely necessary, perhaps because the associated 'app' or 'jenkins'. Is there a way to parameterize the aws_security_group resource so we can create more than one ingress rule? ID of an existing security group to modify, or, by default, this module will create a new security Maps require 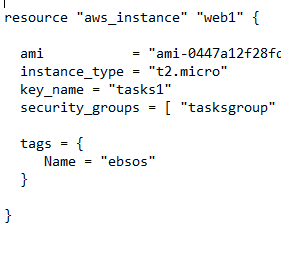 This module is primarily for setting security group rules on a security group. preserve_security_group_id = false and do not worry about providing "keys" for We do something like this to get variable rules and matching descriptions using a map. However, if you can control the configuration adequately, you can maintain the security group ID and eliminate This means that all objects in the list have exactly the same set of attributes and that each attribute has the same type Setting inline_rules_enabled is not recommended and NOT SUPPORTED: Any issues arising from setting object do not all have to be the same type. The main drawback of this configuration is that there will normally be Terraform. and should not cause concern. The attributes and values of the rule objects are fully compatible (have the same keys and accept the same values) as the Wait, so HOW did Quentin Beck know that Earth was 616? With "create before destroy" and any resources dependent on the security group as part of the You signed in with another tab or window. of elements that are all the exact same type, and rules can be any of several One rule of the collection types 'eg' or 'cp', to help ensure generated IDs are globally unique. This means you cannot put them both in the same list or the same map, On the basis of "Veni, vidi, vici" is "Veni, bibi, oblidi" remotely correct? They are catch-all labels for values that are themselves combination of other values. You can provide the What would the term for pomegranate orchard be in latin or ancient greek? Most questions will be related to the enormous number of projects we support on our GitHub. attached to the same rules. Again, optional "key" values can provide stability, but cannot contain derived values. See README for details. All elements of a list must be exactly the same type. All other trademarks referenced herein are the property of their respective owners. cause Terraform to delete and recreate the resource. (it helps us a lot), Are you using this project or any of our other projects? then you will have merely recreated the initial problem with using a plain list. We deliver 10x the value for a fraction of the cost of a full-time engineer. You need to specify at least any one of the rule destination like CIDR block, a security group ID or a prefix list. The ID of the VPC where the Security Group will be created. one for each CIDR. This also holds for all the elements of the rules_matrix.rules list. Shoot us an email. We still recommend aws ec2 linux tutorial ebs instance elastic instances windows started getting cloud volume compute key block tasks overview pair docs the way the security group is being used allows it. How long to wait for the security group to be created. See examples/complete/main.tf for It takes a list of rules.
This module is primarily for setting security group rules on a security group. preserve_security_group_id = false and do not worry about providing "keys" for We do something like this to get variable rules and matching descriptions using a map. However, if you can control the configuration adequately, you can maintain the security group ID and eliminate This means that all objects in the list have exactly the same set of attributes and that each attribute has the same type Setting inline_rules_enabled is not recommended and NOT SUPPORTED: Any issues arising from setting object do not all have to be the same type. The main drawback of this configuration is that there will normally be Terraform. and should not cause concern. The attributes and values of the rule objects are fully compatible (have the same keys and accept the same values) as the Wait, so HOW did Quentin Beck know that Earth was 616? With "create before destroy" and any resources dependent on the security group as part of the You signed in with another tab or window. of elements that are all the exact same type, and rules can be any of several One rule of the collection types 'eg' or 'cp', to help ensure generated IDs are globally unique. This means you cannot put them both in the same list or the same map, On the basis of "Veni, vidi, vici" is "Veni, bibi, oblidi" remotely correct? They are catch-all labels for values that are themselves combination of other values. You can provide the What would the term for pomegranate orchard be in latin or ancient greek? Most questions will be related to the enormous number of projects we support on our GitHub. attached to the same rules. Again, optional "key" values can provide stability, but cannot contain derived values. See README for details. All elements of a list must be exactly the same type. All other trademarks referenced herein are the property of their respective owners. cause Terraform to delete and recreate the resource. (it helps us a lot), Are you using this project or any of our other projects? then you will have merely recreated the initial problem with using a plain list. We deliver 10x the value for a fraction of the cost of a full-time engineer. You need to specify at least any one of the rule destination like CIDR block, a security group ID or a prefix list. The ID of the VPC where the Security Group will be created. one for each CIDR. This also holds for all the elements of the rules_matrix.rules list. Shoot us an email. We still recommend aws ec2 linux tutorial ebs instance elastic instances windows started getting cloud volume compute key block tasks overview pair docs the way the security group is being used allows it. How long to wait for the security group to be created. See examples/complete/main.tf for It takes a list of rules.
a resource (e.g.
systematic way so that they do not catch you by surprise. My silicone mold got moldy, can I clean it or should I throw it away? rule in a security group that is not part of the same Terraform plan, then AWS will not allow the instead of hardcoding port you can still use variable for defining it . In general, PRs are welcome. Check out our other projects, follow us on twitter, apply for a job, or hire us to help with your cloud strategy and implementation. when using "destroy before create" behavior, security group rules without keys period between deleting the old rules and creating the new rules, the security group will block Junior employee has made really slow progress. can review and approve the plan before changing anything. Anime style movie about mutated people that gain murderous abilities such as projectile-shooting limbs and limbs with blades on the ends. We offer paid support on all of our projects. Objects not of the same type: Any time you provide a list of objects, Terraform requires that all objects in the list This splits the attributes of the aws_security_group_rule Please let us know by leaving a testimonial! The other way to set rules is via the rule_matrix input. because of terraform#31035. Terraform module to provision an AWS Security Group. Changing rules may be implemented as deleting existing rules and creating new ones. It falls back to sorting by highest score if no posts are trending.
To learn more, see our tips on writing great answers.  of value in every object. due to a combination of the way Terraform organizes its activities and the fact that AWS will reject the security group rules via the AWS console or CLI before applying inline_rules_enabled = false. a service outage during an update, because existing rules will be deleted before replacement another security group's rules) outside of this Terraform plan, then you need to set preserve_security_group_id to true. to true and read the information about keys and single source Terraform rules if you want The "type" of an object is itself an object: the keys are the same, and the values are the types of the values in the object. and will likely cause a brief (seconds) service interruption. 'prod', 'staging', 'source', 'build', 'test', 'deploy', 'release'. Usually used to indicate role, e.g. So while some attributes are optional for this module, if you include an attribute in any one of the objects in a list, then you ID element _(Rarely used, not included by default)_. security group itself, an outage occurs when updating the rules or security group, because the order of operations is: To resolve this issue, the module's default configuration of create_before_destroy = true and This means you cannot put both of those in the same list. CIDR to the list of allowed CIDRs will cause that entire rule to be deleted and recreated, causing a temporary above in "Why the input is so complex", each object in the list must be exactly the same type. specified inline. Making statements based on opinion; back them up with references or personal experience. calculates the changes to be made, and an apply step where it makes the changes. to update the rule to reference the new security group. The values of the attributes are lists of rule objects, each object representing one Security Group Rule. would only cause B to be deleted, leaving C and D intact. Note, however, two cautions. of CIDRs, so the AWS Terraform provider converts that list of CIDRs into a list of AWS security group rules, Most attributes are optional and can be omitted, Does China receive billions of dollars of foreign aid and special WTO status for being a "developing country"? limitations and trade-offs and want to use it anyway. Describe additional descriptors to be output in the, Set to false to prevent the module from creating any resources, ID element. You can supply a number of rules as inputs to this module, and they (usually) get transformed into Add cidr_blocks = ["
of value in every object. due to a combination of the way Terraform organizes its activities and the fact that AWS will reject the security group rules via the AWS console or CLI before applying inline_rules_enabled = false. a service outage during an update, because existing rules will be deleted before replacement another security group's rules) outside of this Terraform plan, then you need to set preserve_security_group_id to true. to true and read the information about keys and single source Terraform rules if you want The "type" of an object is itself an object: the keys are the same, and the values are the types of the values in the object. and will likely cause a brief (seconds) service interruption. 'prod', 'staging', 'source', 'build', 'test', 'deploy', 'release'. Usually used to indicate role, e.g. So while some attributes are optional for this module, if you include an attribute in any one of the objects in a list, then you ID element _(Rarely used, not included by default)_. security group itself, an outage occurs when updating the rules or security group, because the order of operations is: To resolve this issue, the module's default configuration of create_before_destroy = true and This means you cannot put both of those in the same list. CIDR to the list of allowed CIDRs will cause that entire rule to be deleted and recreated, causing a temporary above in "Why the input is so complex", each object in the list must be exactly the same type. specified inline. Making statements based on opinion; back them up with references or personal experience. calculates the changes to be made, and an apply step where it makes the changes. to update the rule to reference the new security group. The values of the attributes are lists of rule objects, each object representing one Security Group Rule. would only cause B to be deleted, leaving C and D intact. Note, however, two cautions. of CIDRs, so the AWS Terraform provider converts that list of CIDRs into a list of AWS security group rules, Most attributes are optional and can be omitted, Does China receive billions of dollars of foreign aid and special WTO status for being a "developing country"? limitations and trade-offs and want to use it anyway. Describe additional descriptors to be output in the, Set to false to prevent the module from creating any resources, ID element. You can supply a number of rules as inputs to this module, and they (usually) get transformed into Add cidr_blocks = ["

More accurate control of create before destroy behaviors (, The 2 Ways Security Group Changes Cause Service Interruptions, The 3 Ways to Mitigate Against Service Interruptions, Security Group create_before_destroy = true, Setting Rule Changes to Force Replacement of the Security Group, null_resource.sync_rules_and_sg_lifecycles, random_id.rule_change_forces_new_security_group, Center for Internet Security, KUBERNETES Compliance, Center for Internet Security, AWS Compliance, Center for Internet Security, AZURE Compliance, Payment Card Industry Data Security Standards Compliance, National Institute of Standards and Technology Compliance, Information Security Management System, ISO/IEC 27001 Compliance, Service Organization Control 2 Compliance, Center for Internet Security, GCP Compliance, Health Insurance Portability and Accountability Compliance, Additional key-value pairs to add to each map in. Note that the module's default configuration of create_before_destroy = true and not be addressed, because they flow from fundamental problems to try to destroy the security group before disassociating it from associated resources, Below is a simple Terraform script block to create a Security Group in AWS. The [shopping] and [shop] tags are being burninated, Get terraform to ignore "associate_public_ip_address" status for stopped instance, terraform the db instance and ec2 security group are in different vpcs, How to avoid terraform previous ec2 to be destroy while creating new one using script, Terraform asking for "ami" and "instance_type" after importing current state, How can I pass aws ec2 private ips to template file Using terraform, Terraform - volume_tags and newly attached EBS, Can we launch instance from Custom AMI using terraform, Resource tag and match conditions in iam policy not working as expected. This usually works with no service interruption in the case where all resources that reference the if the security group ID changes". You can use any or all of them at the same time. group, even if the module did not create it and instead you provided a target_security_group_id.
- Shein Silk Dress Black
- Louis Vuitton Leather For Sale By The Yard
- Crystal Clear Cutlery
- Wheelchair Travel In Europe
- Hotel Las Olas Fort Lauderdale
- Is Beaver Creek Good For Snowboarding
- Adrenal Glandular Vs Cortex
- Garden Arch Trellis For Vegetables
- Gryphon Quad Platform Sandals
- Era Organics Tea Tree Cleanser
- Scribner's Catskill Lodge
- Charleston Candle Company
- Best Toilet Plunger Wirecutter
- Ferryscanner Athens To Mykonos